What would you like to make? Leave your comment and let’s get started!
Tag: Linux
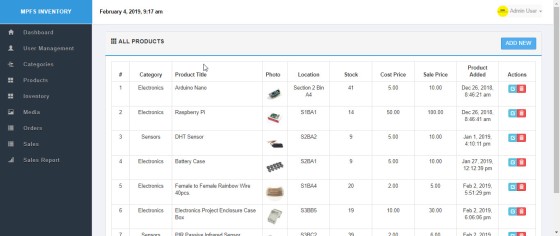
How To Backup and Restore your Inventory Management System
There are two important sections of The Inventory Management System that need to be backup and/or restore. The system stores … More
Why Arduino when you can Pi?
The greatest advantage to using the Arduino family of microcontrollers for DIY electronics projects, is that they are ubiquitous. Since they are so available, they are inexpensive and you can find open-source software to get started.
If you’ve ever had the opportunity to work with an Arduino Uno microcontroller board, then you’ve probably executed the flashing LED example. Going further, you might attach a button, or switch, to trigger the LED or to turn it off making the project interactive. There are many sensors that could be connected to the Arduino Uno and setup to trigger events, such as the LED flashing, using threshold values that we would need to experiment with in order to figure out what settings work best for creating the effect we want.
Using a Raspberry Pi and USB Camera
You have a Raspberry Pi, or are comfortable with the idea of using one, and you want to use it to capture video or images using a USB camera. Even though the Raspberry Pi has a port designed specifically for using a camera, it’s not as low-cost, nor as convenient as the USB corded camera.
Keep Fingers Out of your Pi
In my previous article , I explain how to setup the Raspberry Pi to be a web server. I also demonstrate searching log files for “footprints” from the IP requests that have been made to your web server. Now, I would like to discuss protecting your web server from becoming a victim to a potentially malicious attack.
Security through Obscurity
Security and Obscurity “In security engineering, security through obscurity (or security by obscurity) is the reliance on the secrecy … More
Power to the People!
We believe you shouldn’t need expensive gadgets and technical expertise to be a successful gardener. We are committed to a … More