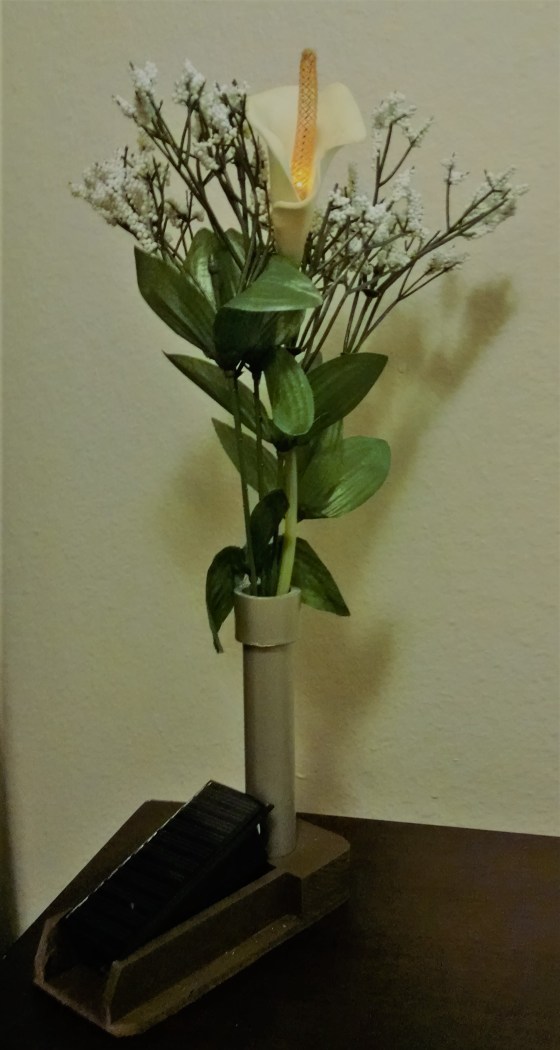You have a Raspberry Pi, or are comfortable with the idea of using one, and you want to use it to capture video or images using a USB camera. Even though the Raspberry Pi has a port designed specifically for using a camera, it’s not as low-cost, nor as convenient as the USB corded camera.
Category: electronics
How do I know if I need to ask for help?
How do I know if I need to ask for help? https://www.linkedin.com/pulse/how-do-i-know-need-ask-help-cory-potter
Making Sound Effects with Arduino
Sound plays an important role in the user experience by adding another layer of depth; making for a more realistic experience.
Hot Stuff
Rather than use a cyanoacrylate or superglue, I use hot glue to keep the connections in place. I used to have a negative perception of using hot glue because it seemed amateur and trashy. After having dismantled many Furbies and Talking Elmos, I see it frequently makes it in the final product. I’ve since reconsidered, and now, I like hot glue because it is convenient and can be removed later if there is a need to check a connection or replace a part.
Arduino FastLED Library
Using an Arduino Uno to calibrate an RGB LED strip.
The purpose of running this example is to determine what settings are needed to use the FastLED library. For this example I’m using an Arduino Uno. The Uno has a ground pin next to pin 13, so for convenience, I’m using pin 13 as a low-current Vcc for the RGB LED lights strip:
Making a Lightshow with Arduino
They are in games, decorations, shadow boxes, sign borders, torches, spotlights, and so on…
Solar-Rechargeable Decorations
Phoenix Fire Lily: Solar rechargeable battery connected to a flickering LED inside an artificial lily flower residing in a hand-crafted wooden vase.
Keep Fingers Out of your Pi
In my previous article , I explain how to setup the Raspberry Pi to be a web server. I also demonstrate searching log files for “footprints” from the IP requests that have been made to your web server. Now, I would like to discuss protecting your web server from becoming a victim to a potentially malicious attack.
Security through Obscurity
Security and Obscurity “In security engineering, security through obscurity (or security by obscurity) is the reliance on the secrecy … More
Power to the People!
We believe you shouldn’t need expensive gadgets and technical expertise to be a successful gardener. We are committed to a … More